Hardening mikrotik and network infrastructure
Posted on 21 June 2025 by Mino — 3 min
In this long blog I try to sum-up some features which you should disable before running MikroTik in any environment. First of all is an backup interface, so in case you lock yourself up, you will always have a way to login. Other points include creating custom user, disabling unused services in various places throughout the RouterOS ;).
Backup interface
Due to a lot of struggle getting all the things "right" with mikrotik and restore did not work some times, I tend to create a backup interface, which in case of lost access has all allow firewall rule and all services are enabled for this interface along with assigned static IP for it.
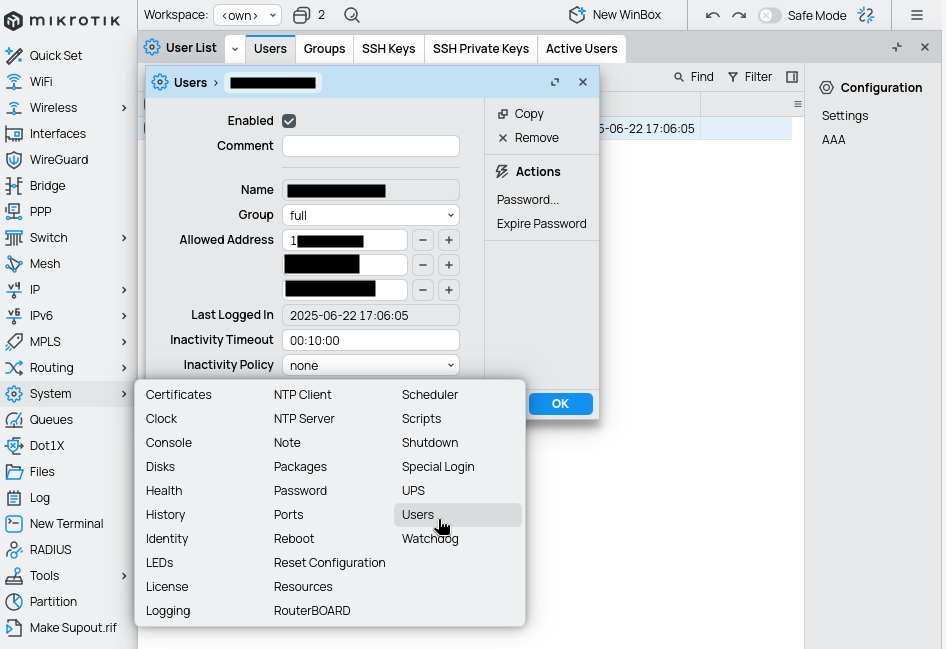
User management
Create new user with random name and long complex password with full privileges to replace the default admin user. Set allowed addresses to only management sub-nets so that not everyone can login using this user.
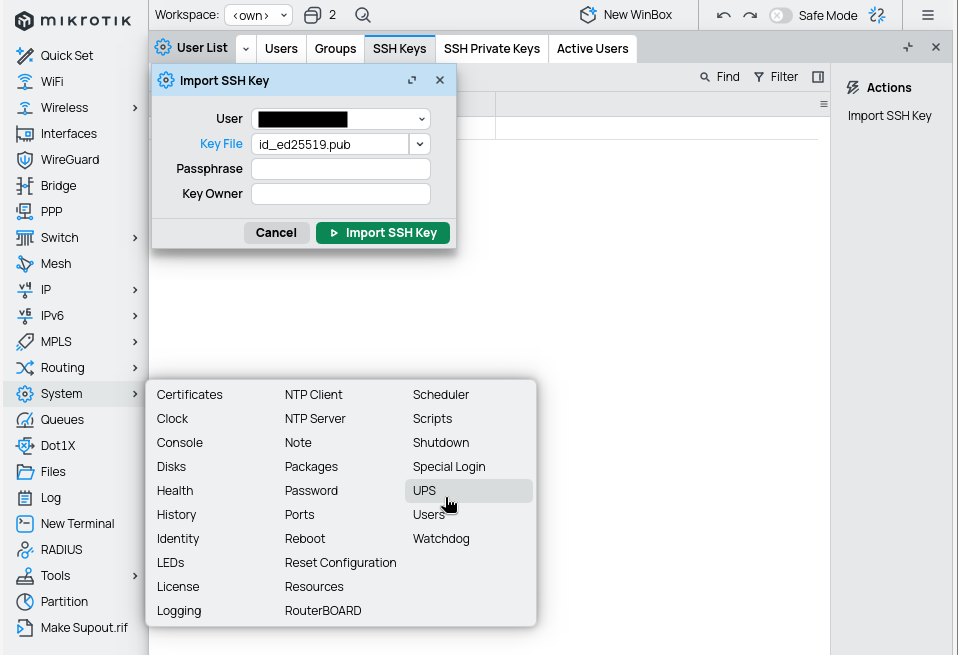
Except complex password also upload SSH public key file to the router OS. After this you can easily import it under ssh keys.
scp ~/.ssh/id_ed25519.pub 192.168.88.1:
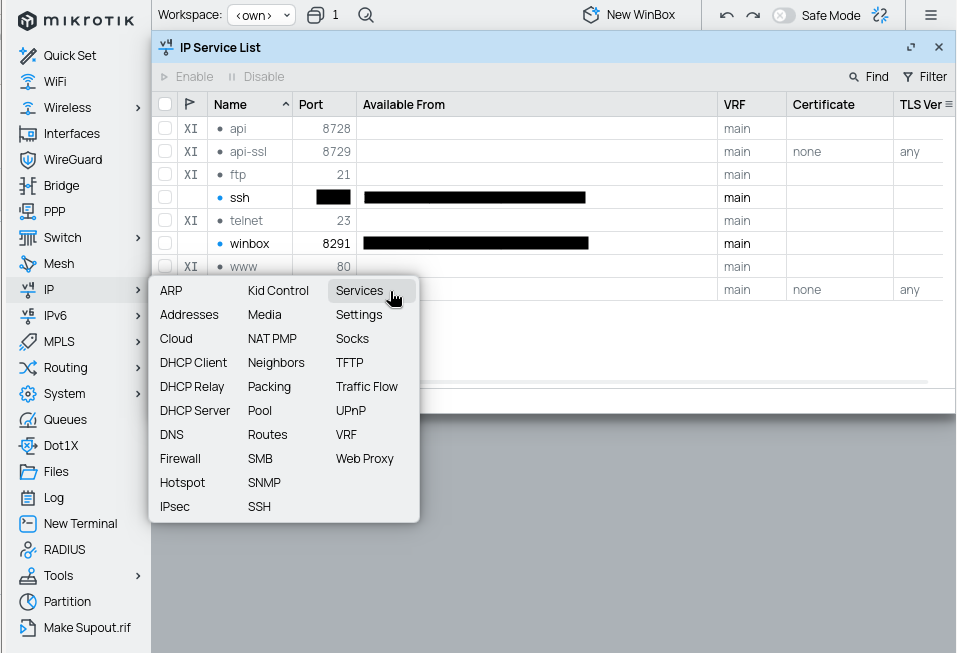
Services
There are multiple locations in which you should disable potentially unwanted services from running.
IP services
IP services hold the most basic services, which can be used to access the Router OS. In this case I disable web interface along with all others, except for WinBox (managing the device) and SSH (automatic backup through scripts). Also don't forget to adjust the allowed IP addresses for each service again, and don't forget to add backup interface / backup IP for access from the backup interface only.
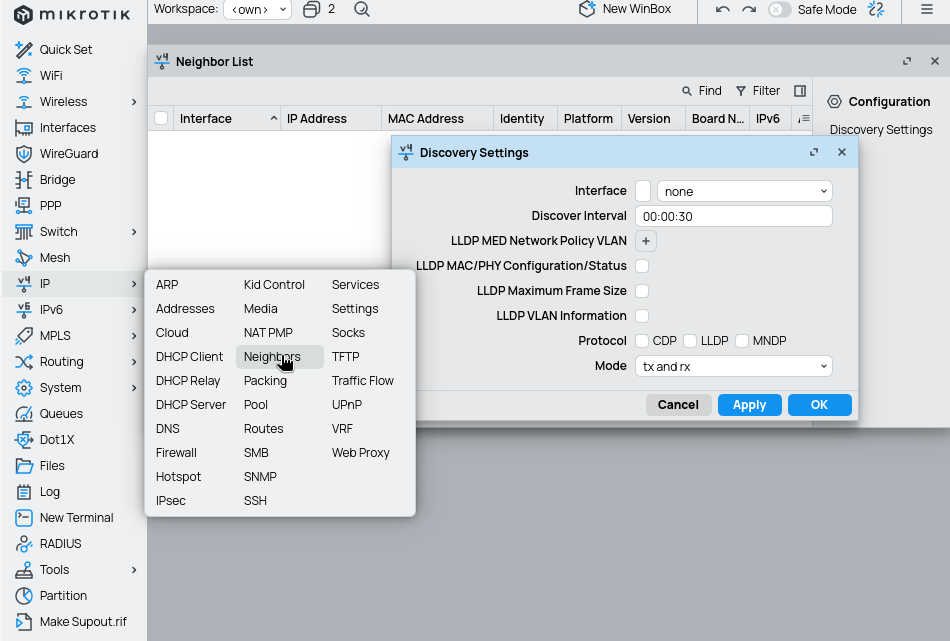
Discovery (CDP, LLDP, MNDP)
Since these protocols often expose critical information about rout device, such as version of your OS, it is really helpful to disable them. Warning: you wont be able to see neighbors in WinBox / device list after disabling these services.
Tools
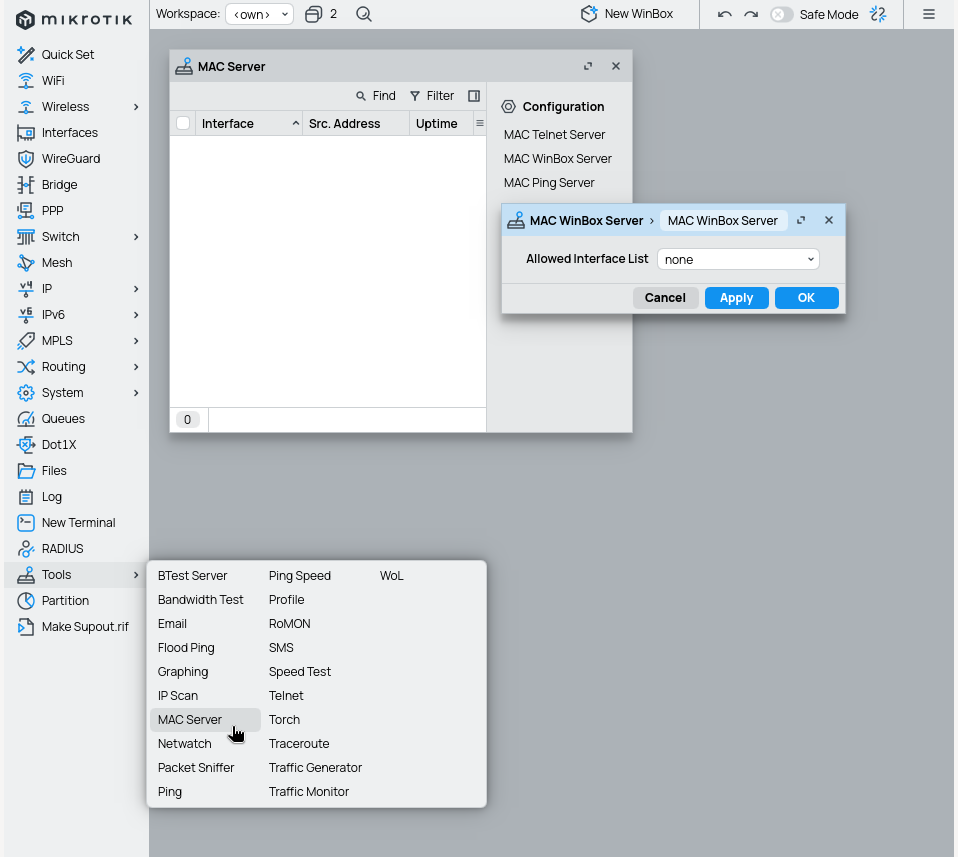
WinBox has a backup option if you mess-up your IP stack that you will be able to login without IP on your device (not so needed if you have a backup interface, and hopefully creating backups is on your regular schedule anyways, you should also disable these services). Warning: you won't be able to login to the device using MAC address anymore. I set all 2 MAC services to none (interface) and set the ping to disabled (unchecked).
Samba
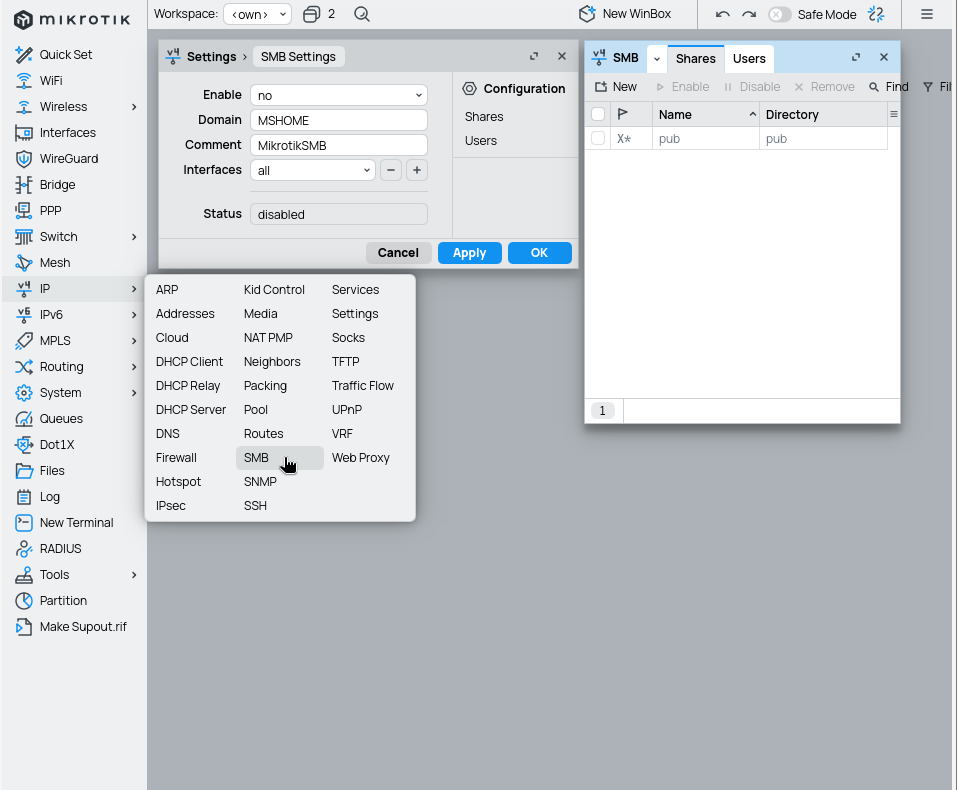
This idea I got from a book about hardening mikrotik and I did not even know that RouterOS offered this option until I read it there. If you were unaware too, just disable it through multiple stages - firewall (allow only dns, winbox and ssh to your router), samba settings themselves and hopefully that is enough ;). Disable everything you find, as the book and my tests conclude that sometime after an update random feature in the SMB gets turned on by itself.
IPv6
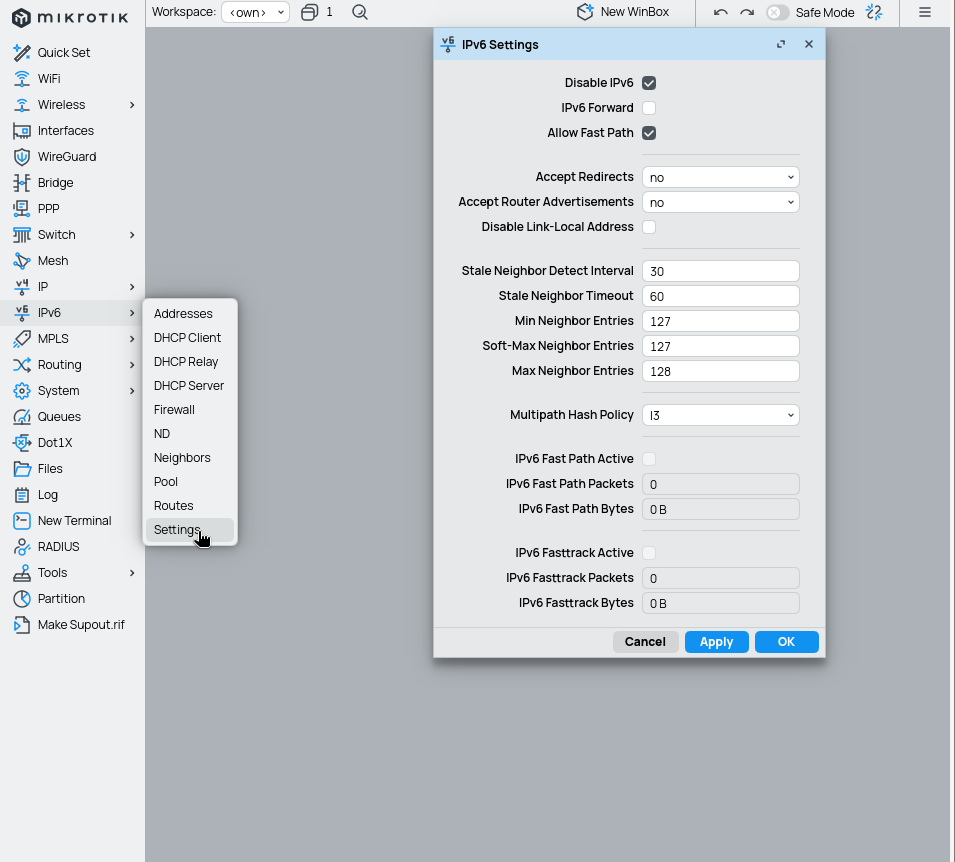
IPv6 is becomming / should be the preferred IP protocol for your network. There exist a lot of reasons on why not to disable v6 (including happy eyeballs, along with some nice meme sites regarding excuses, f.e. https://ipv6bingo.com). However, if you don't use IPv6, then disabling it is a pretty simple step. Either run following command or disable it through Winbox interface as follows.
/ipv6/settings/set disable-ipv6=yes
This post was written without the help of AI.