Useful virtual machine for cyber security - Syslog
Posted on 18 May 2025 by Mino — 3 min

Syslog even as an older technology is still required. For machines or appliances that can't (or I don't want to) install XDR (Wazuh, ...) this variant of monitoring is one of fewer ones left.
Prerequisites
- Software
- [Hardware / VM parameters]
- CPU: 2 i* or ryzen * cores
- RAM: 2GB+
- Disk: 128GB+ (from my experience, I maintain up to 20 hosts - mikrotiks and debians, which get archived daily and produce up to 5MB of compressed data, traffic is low, usage is low, but can serve for someone as a reference, these data get deleted after 180 days automatically)
Syslog-ng
For syslog I use docker deployment. Probably not the simplest idea, but I'm too lazy to change it at this stage. Below is the docker-compose.yml file and under it you can find the configuration for syslog itself.
services:
logs:
image: lscr.io/linuxserver/syslog-ng:latest
container_name: logs
restart: unless-stopped
environment:
- PUID=1000
- PGID=1000
- TZ=Etc/URC
volumes:
- /home/god/config:/config
- /home/god/data:/var/log
ports:
- "10.21.129.21:514:5514/udp"
As a resource for the configuration itself I use syslog-ng and linux man pages.
@version: 4.2
@include "scl.conf"
source s_syslog {
network( ip("0.0.0.0") transport("udp") port("5514") );
};
# Router
destination d_router { file("/var/log/router.log"); };
filter f_router { host("192.168.0.1") or host("router"); };
log { source(s_syslog); filter(f_router); destination(d_router); };
# Switch
destination d_switch1 { file("/var/log/switch.log"); };
filter f_switch1 { host("192.168.5.2") or host("switch"); };
log { source(s_syslog); filter(f_switch1); destination(d_switch1); };
# WiFi
destination d_wifi { file("/var/log/wifi.log"); };
filter f_wifi { host("192.168.4.2") or host("wifi"); };
log { source(s_syslog); filter(f_wifi); destination(d_wifi); };
MikroTik
To properly get all logs from the mikrotik (the default configuration does not log everything).
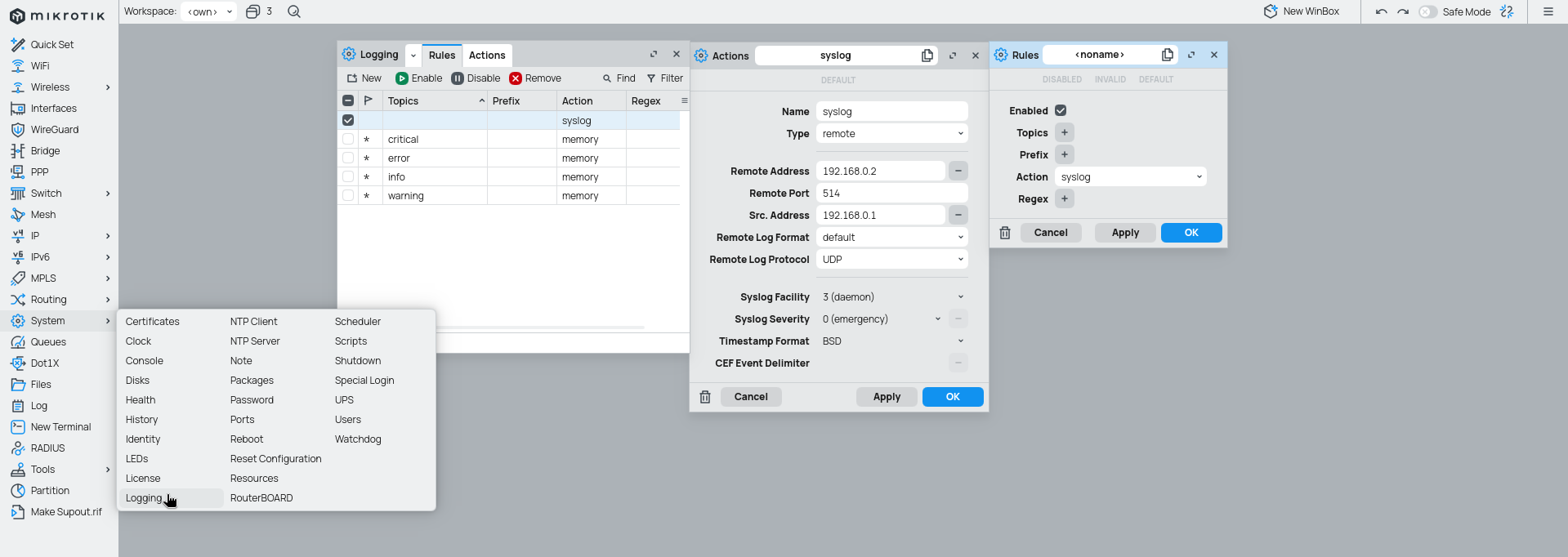
To achieve the same result using console/ssh only use the following sets of commands.
/system/logging/action/add name=syslog target=remote remote=192.168.0
.2 src-address=192.168.0.1 remote-port=514 remote-protocol=udp remote-log-format=default
/system/logging/add action=remote
Debian & Proxmox
For Debian OS (pure debian and proxmox) I run following commands (install rsyslog and set remote address in the configuration).
sudo apt update
sudo apt install -y rsyslog
sudo systemctl enable --now rsyslog
sudo bash -c '
echo "" >> /etc/rsyslog.conf
echo "# Remote system" >> /etc/rsyslog.conf
echo "*.* @10.21.129.21:514" >> /etc/rsyslog.conf
systemctl restart rsyslog.service
'
Docker
Since docker is also capable of logging to remote server, here is the configuration based on docker documentation, which I use.
sudo tee /etc/docker/daemon.json <<EOF
{
"ipv6": false,
"log-driver": "syslog",
"log-opts": {
"syslog-address": "udp://10.21.129.21:514"
}
}
EOF
sudo systemctl restart docker
This post was written without the help of AI.