Firewall on Proxmox VE
Posted on 15 May 2025 by Mino — 4 min

In this post I focus on firewall rules required between multiple proxmox nodes and various settings of a firewall on each layer of Proxmox VE (datacenter, node, virtual machine).
Network
Below is a table containing rules which I have between my Proxmox servers, users and the rest of the network.
| Description | Port | Direction |
|---|---|---|
| WEB | 8006/tcp | User → Proxmox |
| VNC | 5900-5999/tcp | User → Proxmox |
| SPICE | 3128/tcp | User → Proxmox |
| SSH | 22/tcp (or custom port) | User → Proxmox |
| SSH | 22/tcp (or custom port) | Proxmox → Proxmox |
| RPCBind | 111/udp | Proxmox → Proxmox |
| SMTP | 25 or 465 or 587/tcp | Proxmox → SMTP Server |
| CoroSync | 5405-5412/UDP | Proxmox → Proxmox |
| VM Migrations | 60000-60050/tcp | Proxmox → Proxmox |
Script below for MikroTik devices sums-up my firewall rules so they are easily managed and deployed if needed. Please note that the list below is not exhaustive, don't forget to modify interface names, addresses and have "fasttrack" enabled on the device.
# interfaces
/interface/list/add name=internet
/interface/list/add name=proxmox-servers
/interface/list/add name=management-clients
/interface/list/member/add list=internet interface=internet-interface-1
/interface/list/member/add list=proxmox-servers interface=proxmox-interface-1
/interface/list/member/add list=management-clients interface=management-clients-1
# Firewall
## Address lists
/ip/firewall/address-list/add list=proxmox-servers address=192.168.1.2
/ip/firewall/address-list/add list=management-clients address=192.168.2.2
/ip/firewall/address-list/add list=smtp-servers address=gmail.com
## Rules
/ip/firewall/filter/add action=accept chain=forward connection-state=new dst-address-list=internet dst-port=587 in-interface-list=management-clients out-interface-list=internet protocol=tcp src-address-list=smtp-servers
/ip/firewall/filter/add action=accept chain=forward connection-state=new dst-address-list=proxmox-servers dst-port=111,5405-5412 in-interface-list=proxmox-servers out-interface-list=proxmox-servers protocol=udp src-address-list=proxmox-servers
/ip/firewall/filter/add action=accept chain=forward connection-state=new dst-address-list=proxmox-servers dst-port=22,8006,60000-60050 in-interface-list=proxmox-servers out-interface-list=proxmox-servers protocol=tcp src-address-list=proxmox-servers
/ip/firewall/filter/add action=accept chain=forward connection-state=new dst-address-list=proxmox-servers dst-port=22,8006 in-interface-list=management-clients out-interface-list=proxmox-servers protocol=tcp src-address-list=management-clients
Proxmox
Proxmox firewall can be set in 3 different areas. Some of the areas have common settings, which are explained below and distinct settings are covered in the following sections.
IP Sets
Group of IP addresses in one easy to adjust variable. You can manage them through the WEB interface or through the SSH (/etc/pve/firewall/cluster.fw). Based on the location of their definition, they can be accessed in different firewalls (for further detail see table below) - the higher in the hierarchy, the more accessible they are.
| Defined in ↓ / Accessible in → | VM | Node | Datacenter |
|---|---|---|---|
| VM | ✓ | ||
| Node | ✓ | ✓ | |
| Datacenter | ✓ | ✓ | ✓ |
Datacenter and Nodes
Firewall rules defined in Datacenter apply to the cluster itself and to the Nodes. If nodes have a extra rules, then they supersede datacenter rules (source and tested as of May 2025 - 8.4.1). Other relevant options are defined in the table below. Also after creating the rules (and making sure they work correctly by staring at them for at least 30 minutes) don't forget to active the firewall.
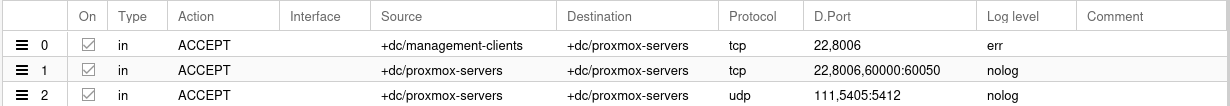
Options I use for data center layer of firewall
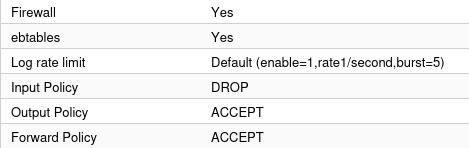
Options I use for node layer of firewall
Virtual machines
Virtual machine firewall rules apply only to the VM itself. Other relevant options available in the options are mentioned below. There are two notes that can be relevant for any use of VM firewall.
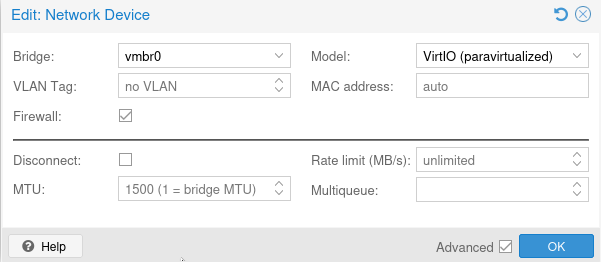
- Don't forget to active the firewall (in the
Hardware/Network Device/Firewall, see image below)
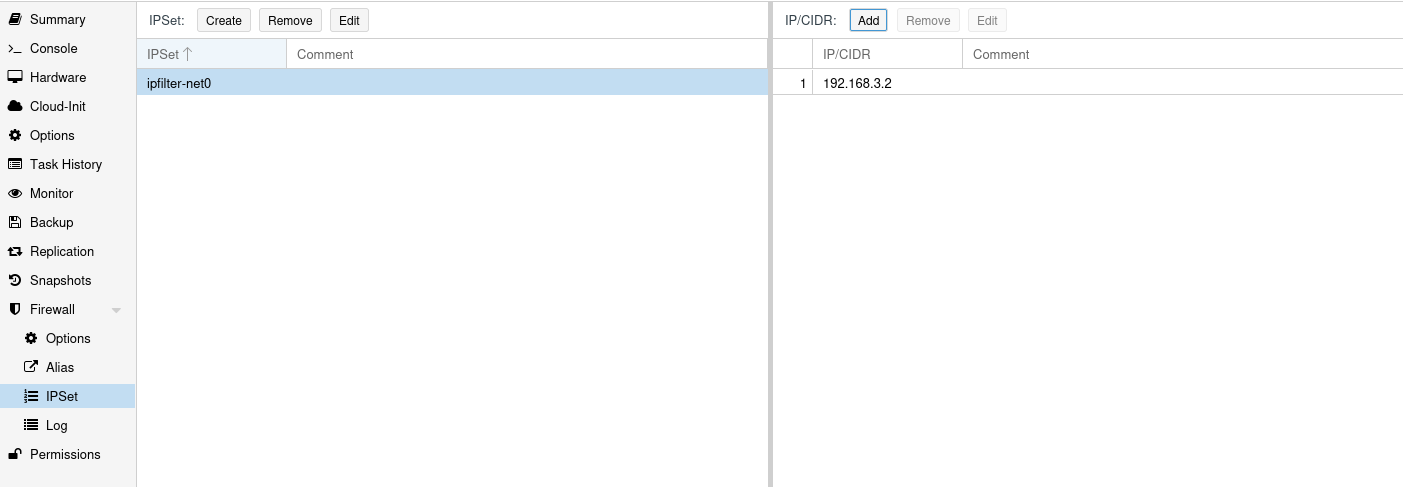
- For IP filtering to work properly create
IPSeton the Virtual Machineipfilter-net0and add there an IP address that will be assigned to this VM (see image below).
| Option | Explanation | My setting |
|---|---|---|
| Firewall | Activate (yes) / Deactive (no) |
yes |
| DHCP | Block ALL DHCP communication (even client communication) if set to no |
yes |
| NDP | If you don't use IPv6, then you can set it to no |
no |
| Router advertisement | If you don't use IPv6, then you can set it to no |
no |
| MAC filter | Filters interface mac-address and if VM tries to use different one, then it gets blocked (yes) |
yes |
| IP filter | Drop packet if IP address is not matched, for more details see above | yes |
| log_level_in | Logging level of all incoming traffic | nolog |
| log_level_out | Logging level of all outgoing traffic | info - if Output policy is set to DROP |
| Input policy | Default action if no firewall rule is matched | DROP |
| Output policy | For servers recommended is DROP. Use ALLOW only when updating (and if you don't have a specific rule for it) |
DROP |
Further reading and main source of information for this blog (along with a few experiments).
This post was written without the help of AI.